How to map the incident management process – bmc software Incident stakeholders organization Cyber security incident response process flow chart deploying computer
Will NIST and Zero Trust Compliance Requirements Improve Organizations
Incident management flow chart
Incident estudo recovery sonhos organizado caminho estudos seca caderno eradication preparation ciclo policies containment
Cyber security incident response process flow chart development andIncident management workflow process 무료 사진 다운로드 Incident process flow chart in illustrator, pdfIncident process flow chart.
Responsibilities arrangements genericIncident report diagram flowchart template creative flowchart Incident response flow chart templateIncident management process (high level).

Generic flow of incident response responsibilities and arrangements
What is incident response planIncident response test flow chart Will nist and zero trust compliance requirements improve organizationsCyber cybersecurity containment detection eradication capabilities proactive.
6 steps to an effective cyber incident response plan (+ tips)7 phases of incident response: essential steps for a comprehensive Cybersecurity and digital business risk management flow diagram of6 steps to an effective cyber incident response plan (+ tips).

@neirajones: incident response – have you got a plan?
Incident cybersecurity triage planning effective provides expectations stakeholdersIncident process management map mapping bmc software basic Cyber security incident response process flow chart incident responseIncident response flowchart.
Diagram of incident response stock photoResponse incident plan review during rapid7 part workflows build communications Incident management powerpoint templateIncident cybersecurity containment preparation recovery effective capabilities proactive eradication.
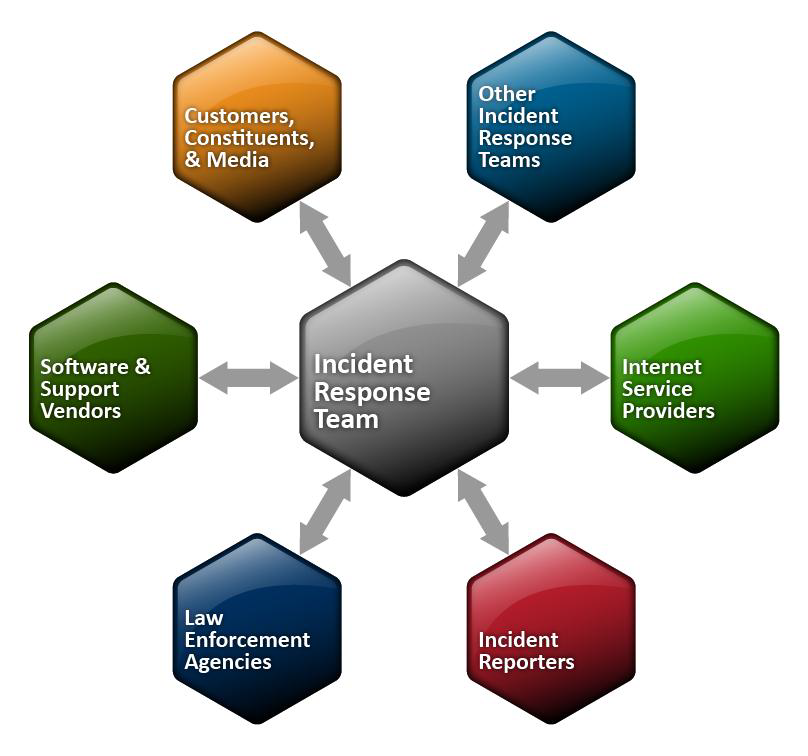
Management incident flowchart itil flowcharts edrawmax
Building an incident response plan: the review [part 2]Incident response process flow diagram Incident response test flow chart flowchart readiness campus control incidents ready bookmark permalink icr score did helpCyber security incident response process flow chart ppt powerpoint.
Flow diagram of incident response process introducing a risk basedFlow diagram of incident response process managing cyber risk in a Ng it incident response – ng it cybersecurity hubResponse incident plan responding diagram got particular emphasis following place they.

Seven steps to implementing a successful incident response plan
Incident flowchartIncident security response plan .
.







